cajkan
Active Member
Hello all,
Looks like Buy Premium feature isnt secure enough.
Today one user purchased premium membership - 52 weeks for only 0.01$
Heres screenshot from E-mail and Paypal:
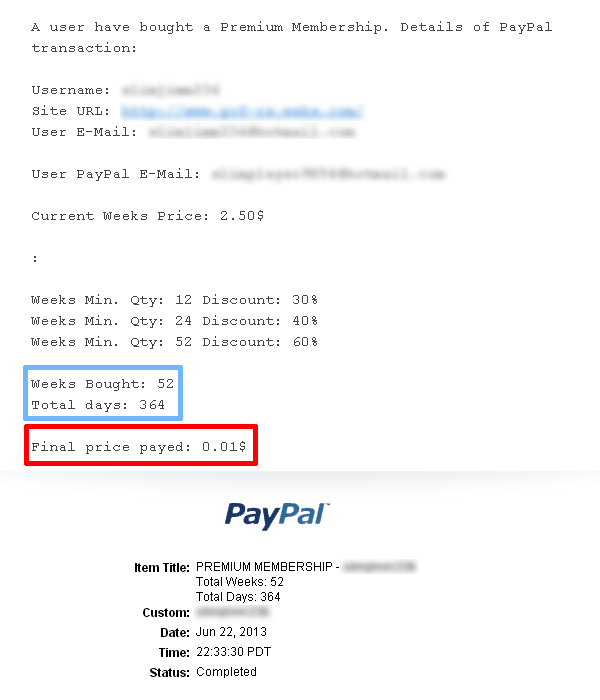
Into screenshot clearly says : 52 weeks - price per week 2.5$.
I dont want to ban / remove user - that will not be the perfect solution coz he can do that again.
I really wanna know, how is this posible and what should be done to aviod this kind of scams.
Thank you
Looks like Buy Premium feature isnt secure enough.
Today one user purchased premium membership - 52 weeks for only 0.01$
Heres screenshot from E-mail and Paypal:

Into screenshot clearly says : 52 weeks - price per week 2.5$.
I dont want to ban / remove user - that will not be the perfect solution coz he can do that again.
I really wanna know, how is this posible and what should be done to aviod this kind of scams.
Thank you


 that is bad advice, PHP encryption is never a solution to weak security. The user can still pass the exact same post/get values to encrypted code and the exploit will still work.
that is bad advice, PHP encryption is never a solution to weak security. The user can still pass the exact same post/get values to encrypted code and the exploit will still work.